How New Technologies Make Computer security Foolproof
In today’s digital landscape, the escalating sophistication of cyber threats demands innovative solutions to safeguard sensitive data, critical infrastructure, and personal information. Integrating cutting-edge technologies has paved the path for a more robust defence against cyberattacks, even while establishing absolutely perfect computer security remains difficult. This article delves into computer security and explores a range of emerging technologies that are reshaping how we protect our digital assets.
Zero Trust Architecture: A Paradigm Shift in Security

The conventional security approach of trusting internal networks and users by default has become obsolete in the face of modern cyber threats. Zero Trust Architecture (ZTA) challenges this paradigm by presuming that no entity, whether inside or outside the organisation, can be trusted inherently. Instead, ZTA implements stringent authentication procedures, access controls, and ongoing monitoring to guarantee that only authorised users have access to sensitive resources. This dynamic approach minimizes the risk of lateral movement by potential attackers, making it a critical component in modern computer security strategies.
AI and Machine Learning: Unveiling Anomalies
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing the computer security landscape by providing the ability to analyze massive volumes of data in real-time. These technologies excel at identifying patterns, anomalies, and potential cyber threats that might go unnoticed by traditional security methods. AI-driven systems can detect unusual user behaviors, monitor network traffic, and assess the risk of incoming files or emails, enhancing threat detection and response capabilities.
IoT Security: Safeguarding the Internet of Things

Securing interconnected devices becomes critical as the Internet of Things (IoT) proliferates. IoT security encompasses encryption, authentication protocols, and continuous monitoring to thwart potential breaches through these connected endpoints.
Supply Chain Security: Guarding Against Third-Party Risks
Modern supply chains encompass various partners, from manufacturers and distributors to software providers and service vendors. This intricate web amplifies the potential entry points for cyberattacks, as each participant in the chain becomes a potential vulnerability. Supply chain attacks are rising, targeting vulnerabilities in third-party software and services. Implementing stringent vendor risk assessments, regular audits, and secure coding practices helps mitigate these risks.
Quantum Encryption: Future-Proofing Security
Current encryption techniques may be threatened by quantum computing. Quantum encryption, which makes use of quantum mechanics, provides unmatched protection against quantum attacks and guarantees long-term data confidentiality. Enter quantum encryption, a revolutionary approach that harnesses the principles of quantum mechanics to create an unbreakable shield against cyber threats. As classical encryption methods face the growing power of quantum computing, quantum encryption emerges as a beacon of hope, promising unparalleled security for the digital age.
Cyber Range Training: Enhancing Cyber Resilience
Cyber range training involves realistic simulations of cyberattacks to train computer security teams in responding effectively. These training scenarios help professionals develop incident response skills and refine their strategies. Cyber range platforms offer diverse systems, from malware infections to advanced, persistent cyber threats. This diversity exposes participants to various attack vectors, enhancing their ability to recognize and counter cyber threats. To perform pen testing or penetration testing of your website and/or mobile applications, please visit our website now.
Deepfake Detection: Unmasking Manipulated Content

Deepfakes are artificial intelligence-generated works of art that convincingly combine the likenesses of two people while maintaining their individuality. Leveraging machine learning and neural networks, these manipulations can convincingly mimic facial expressions, voice, and even mannerisms. The rise of deepfake technology presents challenges in verifying digital content’s authenticity. Deepfake detection tools and algorithms can identify manipulated videos and images to prevent misinformation, fraud, and cyber threats. To get a website for your business which is free of such flaws business click hare.
Physical-Cyber Convergence: Protecting Both Realms

The integration of physical and cyber systems introduces new risks. Ensuring convergence security involves safeguarding digital assets and physical infrastructure, preventing cyber threats and attacks targeting both domains. As physical and digital systems merge, the risks multiply. A breach in one field can cascade into the other, amplifying the potential impact. Cyber threats and attacks, for instance, could have real-world repercussions, such as causing power outages and disruptions when they target a crucial infrastructure like a power system.
Behavioral Biometrics: Unique User Signatures

Through the analysis of individual behaviors including typing speed, mouse movements, and navigation patterns, behavioral biometrics provide a novel method of authentication. This technology creates unique user signatures, making it difficult for cybercriminals to impersonate legitimate users. By continuously monitoring these behavioral traits, organizations can detect unauthorized access attempts or account takeovers in real time, bolstering cyber security at the user level.
End-to-End Encryption: Securing Data Lifecycle
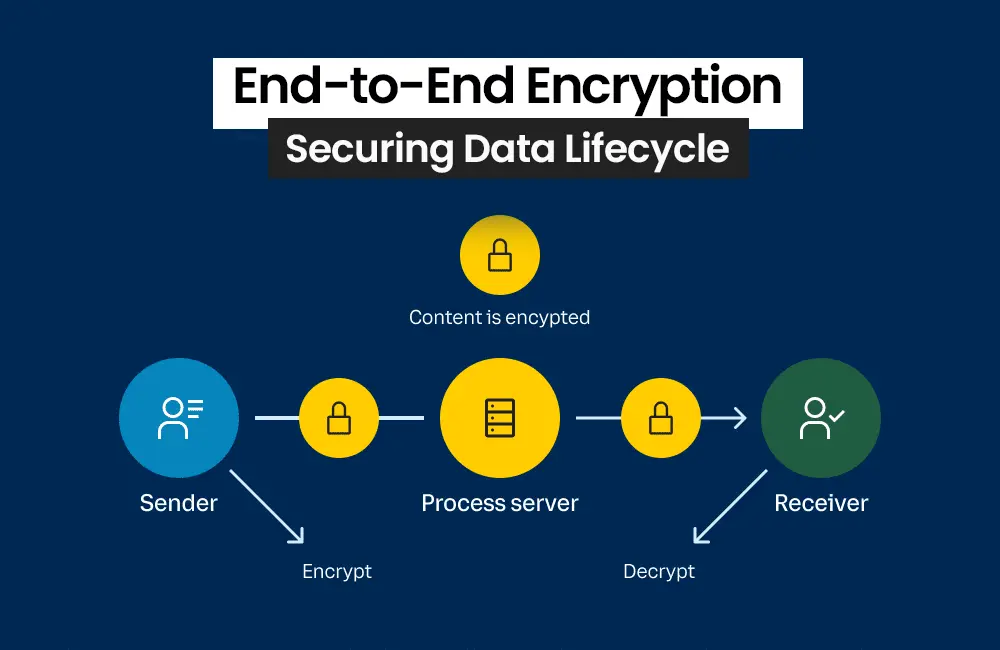
End-to-end encryption has emerged as a fundamental technology for securing data at all stages of its lifecycle. Through the use of this method, data is kept encrypted during processing, transport, and storage, making it unreadable by unauthorized parties. Additional security against data breaches is provided by the fact that even in the event of a breach, the stolen data is worthless without the encryption keys.
Multi-Factor Authentication (MFA): Reinforcing Access Control
Passwords alone are no longer sufficient to guarantee secure access. Multi-factor authentication (MFA) adds extra layers of protection by requiring users to provide multiple verification forms before gaining access to systems or applications. This could involve something the user knows (password), something the user has (a smartphone), and something the user is (biometric data). MFA significantly reduces the risk of unauthorized access, even if passwords are compromised.
Blockchain Technology: Tamper-Resistant Security
Blockchain, renowned for securing cryptocurrencies, has found application in various computer security domains. Its decentralized and tamper-resistant nature makes it ideal for securing transactions, records, and identities. Blockchain can create an immutable audit trail, reducing the risk of unauthorized alterations and enhancing the overall security of digital interactions.
Container Security: Safeguarding Applications
The rise of containerization has transformed software development practices, but it has also introduced new security challenges. Container security tools focus on safeguarding the integrity and isolation of containerized applications. By identifying vulnerabilities, enforcing access controls, and monitoring container behavior, these tools help prevent breaches within containerized environments. Do you want to know more about new computer security vulnerabilities? Click here.
Cloud Security: Navigating the Cloud Safely

As organizations increasingly adopt cloud services, robust cloud security measures become paramount. Cloud Access Security Brokers (CASBs) monitor and manage cloud-related cyber threats, providing visibility into cloud usage, enforcing data protection policies, and detecting unauthorized activities. These technologies ensure that sensitive data remains secure even when stored or processed in cloud environments.
Deception Technology: Misleading Attackers

Deception technology introduces an intriguing concept of confusing attackers by creating decoys, false credentials, and misleading information. By diverting cybercriminals’ attention from critical assets, organizations gain valuable time to detect and neutralize cyber threats. Deception technology plays a strategic role in enhancing incident response and threat mitigation strategies.
Vulnerability Scanning and Patch Management: Staying Updated
Automated vulnerability scanning tools continuously assess systems and networks for potential weaknesses. Combined with effective patch management practices, organizations can promptly address vulnerabilities and apply security updates. This proactive approach reduces the window of opportunity for attackers to exploit known vulnerabilities.
Software-Defined Perimeter (SDP): Dynamic Access Control
The Software-Defined Perimeter (SDP) model offers dynamic and fine-grained access control by creating secure connections between users and resources. It ensures that only authorized users can access specific resources based on contextual factors. SDP minimizes exposure to potential cyber threats and helps organizations enforce access policies without relying solely on traditional perimeter defenses.
Computer security Orchestration and Automation: Swift Incident Response
The speed at which cyber incidents unfold requires efficient incident response mechanisms. computer security orchestration and automation streamline response workflows by automating routine tasks, enabling rapid threat containment, and ensuring consistent actions during security incidents. This technology reduces human error and accelerates incident resolution.
Biometric Authentication: Unique Identity Verification
Biometric authentication leverages unique physical traits such as fingerprints, facial features, and iris patterns for identity verification. These traits are difficult to replicate, making biometric authentication a robust method to prevent unauthorized access. From smartphones to secure facilities, biometrics provide a secure and convenient means of authentication.
Automating Incident Response
Computer security orchestration and automation streamline incident response processes. Automated workflows can rapidly detect, analyze, and respond to security incidents, minimizing response times and ensuring consistent actions.
Network Segmentation: Containing Breaches
Network segmentation divides a network into smaller, isolated segments, limiting the potential impact of a breach. Even if attackers gain access to one segment, they face barriers when attempting to move laterally within the network. This approach enhances network security by minimizing an attacker’s ability to traverse the infrastructure.
Threat Intelligence Platforms: Staying Ahead

Threat intelligence platforms gather, analyze, and disseminate information about current and potential cyber threats. Organizations can proactively adjust their security strategies, fortify defenses, and effectively mitigate cyber risks by staying informed about emerging attack vectors.
Conclusion
The strategies used by cyber enemies change along with the digital environment. Although perfect cyber security is still unachievable, using these cutting-edge technology offers a potential way ahead. By combining advanced AI, behavioral analysis, encryption, and more, organizations can build resilient computer security frameworks capable of adapting to the evolving threat landscape. It’s crucial to remember that while these technologies significantly improve security, computer security is a comprehensive endeavor that also includes personnel training, strong regulations, and a dedication to constant risk assessment. Through a combination of advanced technologies and comprehensive strategies, we can collectively strive for a safer and more secure digital future.
