Safeguarding Network: Fixing Junos OS Vulnerabilities in J-Web
In today’s interconnected digital age, network security isn’t just a priority; it’s a necessity. The modern cyberspace landscape is a dynamic environment filled with potential threats, both known and emerging. To effectively counter these threats, organizations must remain vigilant and proactive in securing their network infrastructure. Recently, Juniper Networks, a prominent provider of networking solutions, issued a critical security bulletin, shedding light on multiple vulnerabilities within their Junos operating system (OS), focusing specifically on the J-Web interface. In this comprehensive blog post, we will delve deep into these vulnerabilities, their potential implications, and explore the crucial steps you can take to mitigate these risks, fortify your network, and ensure the safety of your digital assets.
Understanding the Backbone: Junos OS

Before we dive into the specifics of the vulnerabilities and their resolutions, it’s essential to grasp the significance of Junos OS. Junos stands as the robust and versatile operating system that powers Juniper Networks’ diverse range of devices, including routers, switches, and security appliances. Renowned for its security features, Junos OS is a preferred choice for numerous organizations worldwide.
The Role of J-Web
J-Web, short for Junos Web Management, plays a pivotal role in simplifying the management and configuration of Junos OS devices. It achieves this through a user-friendly graphical interface, making device management more accessible for network administrators and IT professionals. However, this convenience comes with certain security vulnerabilities that must not be ignored.
Vulnerability 1: Unauthorized Access

One of the primary vulnerabilities within J-Web is unauthorized access. This means that malicious actors might exploit this vulnerability to gain unauthorized entry into your network infrastructure. The implications of such unauthorized access are profound and often extend far beyond the initial breach. Now you can read more about Top 9 New Cybersecurity Vulnerabilities to Watch Out for in 2023 by clicking here.
Unauthorized access can allow attackers to:
- Retrieve sensitive data: Once inside, attackers can access confidential information, including user credentials, financial data, or intellectual property.
- Modify configurations: Attackers may tamper with network configurations, potentially leading to service disruptions or data manipulation.
- Launch further attacks: Unauthorized access can serve as a foothold for attackers to conduct more extensive and damaging attacks within your network.
To protect against unauthorized access, it's essential to:
- Implement strong password policies: Enforce complex password requirements and regular password changes to make it harder for attackers to guess or crack passwords.
- Use multi-factor authentication (MFA): Require users to provide multiple forms of verification, such as a password and a onetime code, to access sensitive systems.
- Regularly review and update access controls: Continuously assess and update your access control policies to ensure they reflect the changing security landscape.
Vulnerability 2: Remote Code Execution

One of the critical vulnerabilities associated with J-Web is remote code execution. If successfully exploited, attackers could execute arbitrary code on the vulnerable devices, potentially leading to a complete compromise of your network. Such a breach could be disastrous for any organization, causing significant disruptions and financial losses.
Remote code execution can enable attackers to:
- Gain full control: Attackers can potentially take over the compromised devices, allowing them to manipulate configurations, disrupt services, or install malware.
- Exfiltrate data: Attackers can steal sensitive data or intellectual property from your network, compromising the confidentiality and integrity of your information.
- Establish persistence: Successful code execution might allow attackers to maintain a persistent presence in your network, posing an ongoing threat.
To defend against remote code execution, consider these measures:
- Regularly update your systems: Stay up to date with security patches and updates provided by Juniper Networks to address known vulnerabilities.
- Implement intrusion detection and prevention systems (IDPS): IDPS can help detect and block suspicious network traffic or activities indicative of code execution attempts.
- Conduct regular vulnerability assessments: Periodically assess your network for vulnerabilities and address them promptly to reduce the risk of exploitation.
The Consequences of Inaction
Understanding these vulnerabilities is only half the battle. To appreciate the gravity of the situation, one must consider the potential consequences of inaction when these vulnerabilities are left unaddressed:
Data Breaches

Unauthorized access to your network can cause data breaches, potentially exposing sensitive information. This not only jeopardizes your data but also subjects your organization to potential legal consequences, especially if the data compromised includes customer or client information. Data breaches can lead to:
- Loss of customer trust: Data breaches erode the trust your customers have in your organization, potentially leading to a loss of business.
- Regulatory fines: Depending on your industry, data breaches may subject you to significant fines and legal actions for non-compliance with data protection regulations.
- Reputational damage: Your organization’s reputation can suffer, affecting your brand image and market position.
To mitigate the risk of data breaches, consider the following steps:
- Encrypt sensitive data: Encrypt data both in transit and at rest to protect it from unauthorized access, even if a breach occurs.
- Conduct regular security training: Educate employees about security best practices and the importance of safeguarding sensitive data.
- Implement data loss prevention (DLP) solutions: DLP solutions can help monitor and prevent the unauthorized transfer of sensitive data outside your network.
Network Disruption Due to Vulnerabilities

The ability to execute arbitrary code means that attackers can exploit vulnerabilities in your network operations. This can lead to downtime, which can result in significant financial losses. Network disruptions have cascading effects on an organization’s productivity and profitability, impacting both internal operations and customer service. Network disruptions can result in:
- Financial losses: Downtime can directly translate into financial losses, especially if your organization relies on continuous online operations.
- Customer dissatisfaction: Network disruptions can frustrate customers, affecting their experience and loyalty to your brand.
- Operational challenges: Your organization’s ability to conduct day-to-day business may be severely impacted, causing delays and inefficiencies.
Minimize the impact of network Vulnerabilities, consider the following strategies:
- Implement redundant systems: Use redundancy to ensure that critical network components have backups in case of failure.
- Develop and test disaster recovery plans: Prepare for network disruptions by creating and regularly testing disaster recovery plans.
- Monitor network performance: Implement network monitoring tools to identify and address performance issues before they lead to disruptions.
Vulnerabilities Cause Reputational Damage

A security breach can tarnish your organization’s reputation, eroding trust among customers, clients, and stakeholders. Rebuilding trust can be a time-consuming and challenging endeavor, often requiring extensive communication and remediation efforts. If you want a website and/or mobile application for your business, click here. Reputational damage can lead to:
- Long-term consequences: Reputational damage can have a lasting impact, affecting your organization’s growth and market standing.
- Increased scrutiny: After a security breach, your organization may face increased scrutiny from regulatory bodies, customers, and partners.
- Customer attrition: Loss of trust can result in customer attrition, impacting your revenue and market share.
To safeguard your reputation, consider these steps:
- Transparent communication: In the event of a breach, communicate openly and transparently with affected parties and stakeholders.
- Invest in public relations (PR): Engage PR professionals to manage your organization’s public image during and after a security incident.
- Continuous improvement: Use security incidents as opportunities to learn and improve your organization’s security posture.
Proactive Measures to Eliminate Vulnerabilities
Given the potential consequences, it is essential to adopt a proactive approach to mitigate these risks effectively. Juniper Networks has provided guidance on how to address these vulnerabilities:
Applying Security Updates

The most effective way to protect your devices is to apply security updates promptly. These updates address the identified vulnerabilities and enhance your network’s security. Ensuring a robust and regular update process should be a standard practice within your organization. Regularly check for updates provided by Juniper Networks and apply them to your devices promptly.
When applying security updates:
- Prioritize critical updates: Focus on applying updates that address vulnerabilities with the highest potential impact on your network.
- Test updates in a controlled environment: Before applying updates in production environments, test them in a controlled environment to ensure they do not disrupt operations.
Implementing Network Segmentation
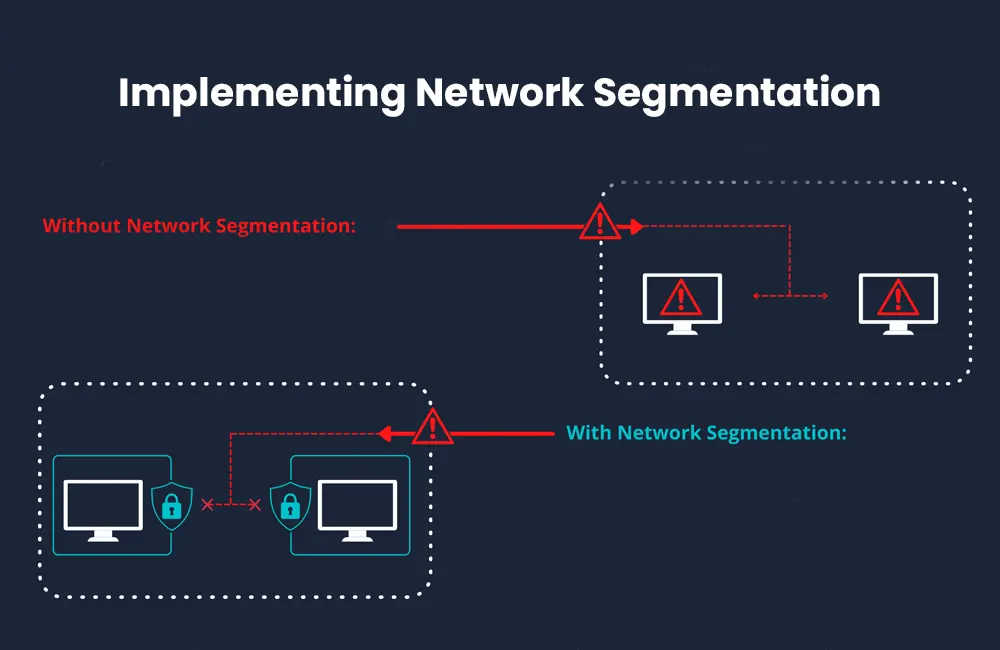
Network segmentation is a crucial step in minimizing the potential impact of a breach by reducing multiple vulnerabilities. By isolating critical systems from less critical ones, you can reduce the attack surface and make it more challenging for attackers to find vulnerabilities and move laterally within your network. Consider implementing strong segmentation strategies and access control policies to ensure that only authorized personnel can access critical areas of your network.
When implementing network segmentation:
- Identify critical assets: Determine which network assets are most critical to your organization’s operations and prioritize their protection.
- Isolate sensitive data: Segregate networks that handle sensitive data to minimize the risk of unauthorized access.
- Monitor inter-segment traffic: Implement monitoring solutions to detect and respond to unusual or suspicious traffic between network segments.
Enhancing Access Control Policies
Review and enhance your access control policies to prevent vulnerabilities exploitation and unauthorized access to your network devices. This includes implementing strong password policies, multi-factor authentication, and conducting regular user access reviews. Ensure that only authorized personnel have access to sensitive areas of your network, and regularly audit and update your access control policies to stay ahead of emerging threats.
When enhancing access control policies:
- Implement multi-factor authentication (MFA): Require users to provide multiple forms of verification, such as a password and a one-time code, to access sensitive systems.
- Enforce least privilege principle: Grant users the minimum level of access necessary to perform their job functions, reducing the potential impact of unauthorized access.
- Conduct regular access reviews: Periodically review and update user access privileges based on their roles and responsibilities within your organization.
Continuous Monitoring to find Possible Vulnerabilities
Implement continuous monitoring to detect vulnerabilities and respond to security incidents in real-time. This proactive approach can significantly reduce the impact of potential breaches by allowing you to identify and mitigate threats as they occur. Utilize advanced monitoring tools and technologies to gain real-time insights into your network’s security posture and act swiftly to address any anomalies or potential threats.
When Executing vulnerability monitoring:
- Define baseline network behavior: Establish a baseline of normal network behavior to help identify deviations that may indicate security incidents.
- Automate threat detection: Use automated threat detection tools to rapidly identify and respond to security threats.
- Develop an incident response plan: Create a comprehensive incident response plan that outlines the steps to take in the event of a security incident and assign roles and responsibilities to your incident response team.
The Road Ahead
In a world where cyber threats continually evolve, staying ahead of vulnerabilities is critical. Junos OS is a robust operating system, but, like any software, it is not immune to security flaws. By understanding the vulnerabilities within J-Web and taking proactive steps to address them, you can protect your organization from potential cyberattacks.
Don’t procrastinate; take action now. Stay informed, keep your devices updated, and bolster your network security measures to safeguard your digital assets. Your network’s security is your responsibility, and proactive measures today can prevent costly consequences tomorrow.
Conclusion
As the digital landscape continues to evolve, network security remains a paramount concern. The vulnerabilities within Junos OS, particularly within the J-Web interface, demand attention and action. Understanding these vulnerabilities, their potential consequences, and the steps required to mitigate them is the first step toward a more secure network environment.
By staying informed, applying security updates, implementing network segmentation, enhancing access control policies, and continuously monitoring your network, you can fortify your defenses and protect your organization from potential threats.






