How Pen Testing Protects Your Business from Cyberattacks
Cybersecurity has become a paramount concern for organizations of all sizes and industries in today’s digital age. The ever-evolving landscape of cyber threats poses a significant risk to the confidentiality, integrity, and availability of sensitive information. In this context, pen testing, also known as penetration testing or ethical hacking, has emerged as a pivotal practice for organizations to defend against cyberattacks proactively. This essay explores the importance of Penetration testing and how it can effectively protect organizations from the constantly evolving threat landscape.
Understanding Pen testing

Pen testing is a proactive cybersecurity approach that involves authorized security experts attempting to exploit vulnerabilities in an organization’s systems, networks, applications, and infrastructure. The primary objective is to identify weaknesses before malicious hackers discover and exploit them. Penetration testing simulates real-world attack scenarios using cybercriminals’ techniques and tools. If you are looking for hidden vulnerabilities in 2023 , click here.
Identifying Vulnerabilities

One of the primary purposes of pen testing is to identify vulnerabilities in an organization’s digital ecosystem. These vulnerabilities can take various forms, such as unpatched software, mis-configured security settings, weak passwords, or flawed network architecture. By systematically searching for these weaknesses, Penetration testing gives organizations a detailed view of their security posture. If you want to identify and safeguard yourself vulnerabilities in J-web? click here.
Assessing Security Controls
Penetration testing evaluates the effectiveness of security controls and measures in place. This assessment includes examining firewalls, intrusion detection systems, access controls, and encryption protocols. By doing so, organizations can gauge how well their current security mechanisms are performing and whether they are adequately protecting against potential threats. Do you want to know about the cybersecurity landscape in 2023? click here.
Prioritizing Remediation Efforts
Once discovered, vulnerabilities are typically ranked based on their severity and potential impact. This prioritization is critical because it enables organizations to allocate resources efficiently. The most critical vulnerabilities can be addressed promptly, reducing the attack surface and minimizing the risk of a successful cyberattack.
Pen Testing Incident Response

An often overlooked aspect of pen testing is the evaluation of an organization’s incident response capabilities. This includes assessing an organization’s ability to detect, respond to, and recover from a cyberattack. By simulating attack scenarios, penetration testing testers help organizations identify weaknesses in their incident response plans and procedures, allowing for necessary improvements. Do you know your mac is also vulnerable to hackers, don’t you? Click here.
Meeting Compliance and Regulatory Requirements
Many industries and sectors have specific cybersecurity regulations and compliance requirements. Pen testing assists organizations in demonstrating their commitment to compliance by actively assessing and addressing security vulnerabilities. This proactive approach helps organizations avoid fines and legal consequences while safeguarding sensitive data from data breaches.
Enhancing User Awareness and Training
Pen testing can also reveal vulnerabilities related to employee awareness and training. For instance, if employees fall victim to social engineering tactics like phishing attacks during testing, it indicates that improved training and awareness programs are needed. Employees are often the first defence against cyber threats, so ensuring they are well-informed is crucial.
Building Trust
Trust has become a valuable currency in an era where data breaches and cyberattacks are frequent headlines. Demonstrating a commitment to cybersecurity through regular penetration testing can enhance trust among customers, partners, and stakeholders. It signals that your organization takes data protection seriously and actively works to secure sensitive information.
Preventing Data Breaches

The most compelling reason to invest in pen testing is its potential to prevent data breaches. Data breaches can result in significant financial losses, reputational damage, and legal consequences. By proactively identifying and mitigating vulnerabilities, organizations can significantly reduce the risk of a breach, sparing themselves the severe consequences of such incidents. To avoide cybersecurity breach and make it foolproof, you must click here.
Continuous Improvement
Cyber threats are dynamic and ever-evolving, necessitating a proactive and adaptive approach to cybersecurity. Pen testing is not a one-time activity; it should be performed regularly to account for changes in an organization’s technology stack and evolving cyber threats. This ongoing process ensures that an organization’s defences remain robust over time.
Competitive Advantage
Organizations prioritizing cybersecurity and demonstrating a solid security posture may gain a competitive advantage. In today’s interconnected world, customers and partners are more likely to trust and engage with businesses that prioritize the security of their data from harmful data breaches. Thus, investment in penetration testing can contribute to business growth and sustainability.
The Pen Testing Process
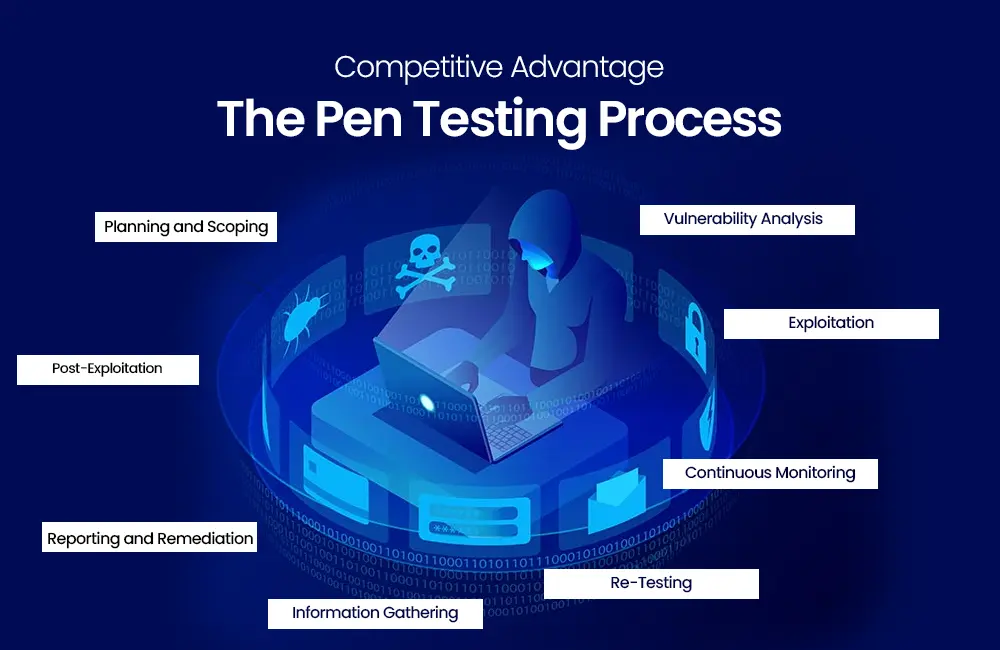
To better understand the practical aspects of pen testing, it is essential to grasp the typical stages of the process:
Planning and Scoping:
The first step involves defining the scope of the pen testing test, including which systems and networks will be tested, what specific goals are to be achieved, and any legal and compliance considerations.
Information Gathering:
Pen testing testers collect information about the target systems and networks, such as IP addresses, domain names, and publicly available information about the organization.
Vulnerability Analysis:
Testers use various tools and techniques to identify vulnerabilities in the target systems. This phase involves scanning for open ports, services, and known vulnerabilities.
Exploitation:
After identifying vulnerabilities, penetration testing testers attempt to exploit them to gain unauthorized access to or control over the target systems. This mimics the actions of a malicious hacker.
Post-Exploitation:
Once access is gained, testers may perform post-exploitation activities to assess the potential impact of an actual cyberattack, such as the exfiltration of sensitive data from harmful data breaches.
Reporting and Remediation:
The findings and results of the pen testing test are documented in a detailed report. This report includes a list of vulnerabilities, their severity, and recommendations for remediation.
Re-Testing:
After remediation efforts are implemented, organizations often re-test to ensure that the identified vulnerabilities have been effectively addressed.
Continuous Monitoring:
In addition to regular pen testing, organizations may implement continuous monitoring solutions to detect and respond to threats in real time.
Choosing the Right Pen Testing Approach
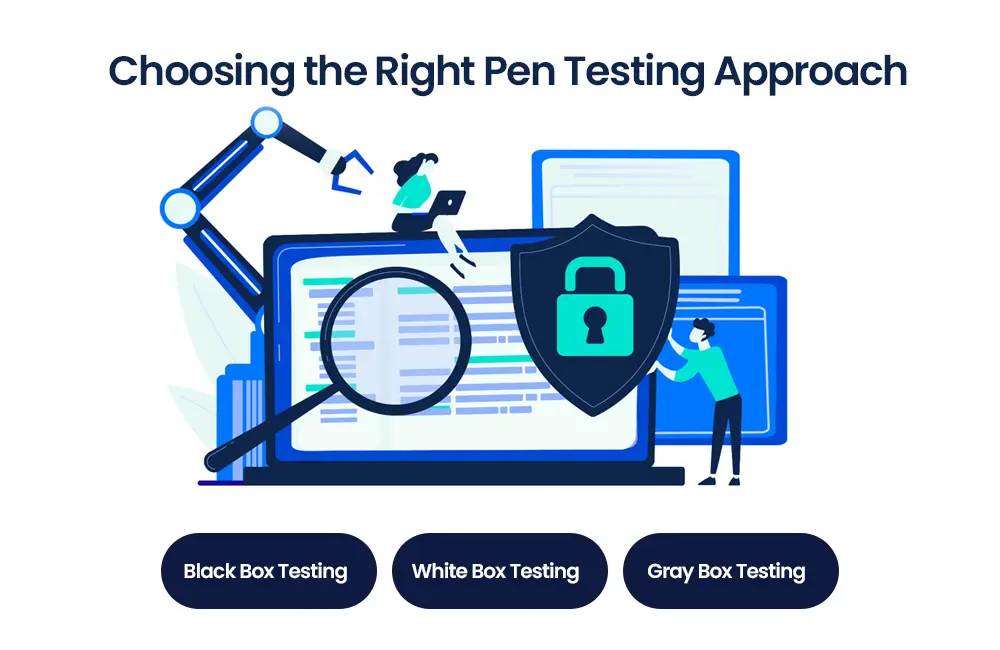
There are several approaches to penetration testing, each with its focus and objectives:
Black Box Testing:
Testers must gain prior knowledge of the organization’s systems and perform testing as an external attacker would.
White Box Testing:
Testers have complete knowledge of the organization’s systems, including network diagrams, source code, and system configurations. This approach allows for a more in-depth assessment.
Gray Box Testing:
Testers partially know the organization’s systems, simulating an insider threat scenario. This approach combines elements of both black-box and white-box testing.
Internal Testing:
External Testing:
Web Application Testing:
Challenges in Pen testing:
Resource Intensity

Pen testing can be resource-intensive, requiring skilled professionals, time, and tools. Smaller organizations may need help to allocate these resources effectively.
Scope Limitations:
The scope of penetration testing must be carefully defined, and it may not cover every potential vulnerability or threat scenario.
Testing Realism:
Achieving realism in testing is essential. The results may be reliable if the test environment accurately reflects the organization’s production environment.
Testing Impact

Sometimes, penetration testing can disrupt normal business operations or cause downtime. Organizations must plan for potential disruptions.
Legal and Ethical Considerations

Engaging in pen testing requires authorization and adherence to legal and ethical guidelines. Unauthorized testing can lead to legal consequences. What if you have a customized website as per your requirements along with absolute updates? To have such a website and/or mobile application, click here.
Conclusion
In conclusion, pen testing is fundamental for organizations seeking to safeguard their digital assets and protect sensitive information from cyber threats. By actively identifying and addressing vulnerabilities, assessing security controls, and enhancing incident response capabilities, organizations can significantly reduce their risk of falling victim to cyberattacks. Moreover, pen testing helps organizations meet compliance requirements, build trust with stakeholders, and gain a competitive advantage in an increasingly interconnected world.
